SAP recently announced its new Fraud Management analytic applications. Currently in “controlled” (limited) release, it’s a promising start for the product and a good example of the type of business process revolution that’s possible when companies can execute complex analytics on big data sets using in-memory and other advanced processing techniques.
SAP recently announced its new Fraud Management analytic applications. Currently in “controlled” (limited) release, it’s a promising start for the product and a good example of the type of business process revolution that’s possible when companies can execute complex analytics on big data sets using in-memory and other advanced processing techniques. Over the next several years a wide swath of basic corporate processes will be transformed by the shift to in-memory processing and big data technology, two key foundational elements of my office of finance research agenda. HANA has been a consistent element of SAP’s product strategy and underlies many recent new releases, such as Business Suite on HANA.
When it pushes the product into general release, SAP will offer three initial flavors of Fraud Management: an insurance claims fraud offering, another designed for use in the public sector and a cross-industry application (for use in, for instance, the purchasing function). It’s likely that quite a few more will follow, given the broad potential use of advanced fraud management analytics. SAP is also focused on developing Fraud Management as a platform that partners can build on to create their own analytical applications that utilize large data sets and in-memory processing for fraud prevention, detection and remediation. I think the fraud management platform has greater long-term potential to drive business for SAP than its internally developed applications because of the requirement for detailed knowledge about how specific types of fraud can be detected in computer systems as well as the need to provision such systems within the context of a company’s unique technology and data infrastructure.
Fraud is a pervasive risk in business. According to the Association of Certified Fraud Examiners the cost is about 5 percent of revenues and therefore a $3.5 trillion annual problem. I’m not sure how much of that is addressable, but for any company the cost of fraud adds up. Fraud exists in internal and external modes and affects all of a company’s facets. Financial fraud can be ruinous to a business. When perpetrated by management it poses reputational risk.
Fraud prevention has been a longstanding corporate activity. In finance, 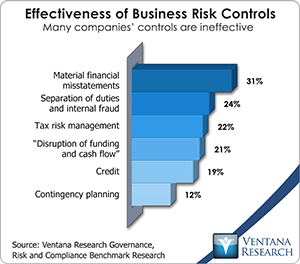 separation of duties and requiring two signatures, for example, are practices designed to keep a single individual from embezzling funds. Multiple invoice matching aims to keep vendors from receiving payment for goods never received. Our research finds that only about one-fourth of companies have adequate controls for separation of duties and internal fraud. Companies conduct internal audits to root out breaches in financial integrity and compliance failures. External auditors exist to provide third-party assurance that attestations to shareholders and other stakeholders are accurate. Forensic accountants are enlisted to document fraud. Managing fraud is a discipline with specialties and subspecialties that reflect the important differences in businesses and the roles of those working in them.
separation of duties and requiring two signatures, for example, are practices designed to keep a single individual from embezzling funds. Multiple invoice matching aims to keep vendors from receiving payment for goods never received. Our research finds that only about one-fourth of companies have adequate controls for separation of duties and internal fraud. Companies conduct internal audits to root out breaches in financial integrity and compliance failures. External auditors exist to provide third-party assurance that attestations to shareholders and other stakeholders are accurate. Forensic accountants are enlisted to document fraud. Managing fraud is a discipline with specialties and subspecialties that reflect the important differences in businesses and the roles of those working in them.
Preventing fraud in public companies’ financial statements was the main point of the Sarbanes-Oxley Act of 2002, passed in the wake of several spectacular management frauds. The act recognized the importance that IT systems play in modern fraud prevention and fraud management. Until the 1990s, computer systems were a point of vulnerability because systems were highly proprietary, companies had only partially automated their businesses, and computing power was expensive, so it was difficult to detect fraud. Since then, though, computer systems have made it much easier to manage fraud. Today, midsize or larger companies perform almost all activities using IT systems that are open and transparent. They achieve a high level of fraud prevention by ensuring that systems are highly tamper-resistant through, for example, identity management – ensuring you are who you say you are. Companies make fraud management more effective by using IT systems to impose controls, automatically test and monitor these controls, and generate automatic alerts and responses when conditions are met.
Fraud detection and prevention is a process of finding needles in haystacks. Today, the largest number of those needles are found based on tips, according to the Association of Certified Fraud Examiners, which credits tips for uncovering 43 percent of corporate frauds. Another 15 percent are found as a result of management reviews and 14 percent from internal audit. IT systems detect just one percent.
It’s probably not feasible and almost certainly not worthwhile to eliminate all business fraud because the cost would exceed the recoverable amount. Up until now, the technology available to analyze data sets for fraud has not had the power to make using it a practical option for broad-based, continuous investigation. The breakthrough that Fraud Management can achieve is to substantially lower the cost of detecting fraud and mitigating its impact. One reason the insurance industry is a likely early adopter is that decades ago it became common for companies to raise the threshold of materiality in examining claims to achieve an appropriate cost/benefit balance. Today, it’s common for insurers to pay a claim automatically where the cost of investigating it is higher than it’s worth. Lowering the cost of investigation through increased automation and factoring in other issues such as the impact of delaying compensationon customer satisfaction could enable insurance companies to reduce payments on fraudulent claims without jeopardizing profitable relationships. In-memory computing of very large data sets can address this issue more efficiently because it has made it both feasible and cost-effective to sift through immense piles of information to detect suspicious items within a reasonable amount of time.
In-memory computing of large data sets also makes organizations more auditable. Utilizing an analytical application makes it possible to detect the electronic equivalent of the erasures, handwriting style discrepancies and different colored inks that were the staples of auditing and accounting fraud risk management in the days of paper ledgers and journals. And utilizing Fraud Management and other similar analytical applications will not necessarily be confined to a reactive mode. The use of predictive analytics with large, real-time data sets makes it possible to detect suspicious activity as it evolves, enabling companies to initiate preventive steps before a fraud has been completed. For example, it should be possible to examine insurance or warranty claims at the time they are submitted to generate a fraud potential score that companies can use to decide whether to pay the claim immediately or investigate further.
While it has substantial potential, SAP faces at least three significant challenges in marketing and selling Fraud Management. First, because the incidence of addressable fraud is widely scattered across an enterprise it can be difficult to identify the natural buyer for the platform. These types of buyers are rarely on the prowl for technology solutions to their business issues. They may not keep up with technology trends, nor would they immediately see the connection between in-memory processing of big data sets and fraud management. Second, the HANA platform is a necessary but insufficient component to fraud management solutions. One of the most challenging aspects of implementing a fraud detection and prevention system is identifying the things that need to be monitored and measured, creating algorithms or describing patterns that define “suspicious” events, items, values, ratios or relationships (to name five), and then defining thresholds and conjoint conditions (to name two) that indicate that an item is worth investigating. Third, fraud detection efficacy is a tradeoff between the percentage of frauds detected and their value balanced against false positives. Perfect detection is likely to be more costly than it is worth because of the effort wasted investigating red herrings. Here again, automating the optimal selection of needles in the haystack is critical. While SAP can create some number of applications to address broad-based needs, it also will need to rely on subject matter experts to implement these applications. Expert organizations will also be able to use the SAP platform to create fraud management applications for individual companies and even specific functions or business units. Fortunately, many of the large audit firms, forensic accountants and specialized fraud consultants with subject matter knowledge have been selling this expertise to natural buyers for decades. These organizations, and others such as insurance companies, have developed a considerable body of knowledge built on decades of experience. They are well positioned to form a productive partner channel with SAP.
However, SAP ultimately will be competing with other software companies (such as IBM, Microsoft and Oracle) for the platform business. To become a preferred solution for consulting and implementation partners, Fraud Management must prove itself to be one that these subject matter experts can readily use to create affordable solutions for their clients. The solutions that these partners provide must also be readily usable by the clients so they can adapt to an evolving fraud landscape and extend their coverage as need arises.
It’s still early days for this promising technology. I’m enthusiastic about its potential, but past experience suggests that it’s wise to temper that enthusiasm. We can only guess at the “gotchas” and other barriers that SAP, other software vendors, partners and customers will encounter as they figure out how to employ the power of in-memory processing of big data and use Fraud Management to reduce costs.







