Secure Video Conferencing
With so many video conferencing options available, it can be difficult to decide on the right solution for your enterprise.…
5 Questions to Ask as You Prepare for a Compliance Audit
For most cloud service providers, a compliance audit is, at best, a necessary evil — the root canal of the…
Why Returning $1 Trillion to Shareholders is a Bad Idea
According to the Financial Times, companies are on record pace to return over one trillion dollars to shareholders this year…
IBM Opens Up Its Threat Data as Part of New Security Intelligence Sharing Platform
IBM has joined an increasing number of vendors who are pushing for real-time cybersecurity information sharing among private and public…
Malicious Tool Provides Attackers with a New Type of Zombies
An interesting concept which has really emerged only lately - IoT, or: “the Internet of Things”, has recently been in…
How to Clean Up the Mess: Surviving a Data Breach
Here’s a scary thought: Nearly half (43%) of all companies experienced a data breach last year, most of which took…
Facebook’s ThreatExchange to Help Cyber Security Experts Coordinate Their Efforts Against Hackers
Hackers continue to target companies throughout the United States with cyber attacks. In 2014, cyber attacks hit a rapid pace…
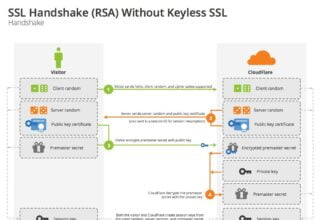
A Look at How Keyless SSL Works
Secure Socket Layer, or SSL for short, is one of the key elements to providing a safe and secure web…
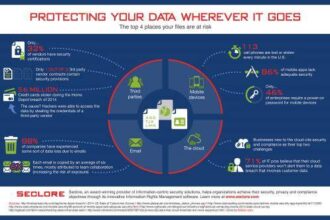
Protecting Your Data Wherever It Goes [INFOGRAPHIC]
Many of today’s businesses have moved on from the large metal filing cabinets of yore, replacing them with digital files,…
From Police to Partner: The Changing Role of IT
When evaluating business applications, the average non-technical employee probably knows as much about security and compliance as he does about…