Companies Without AI-Based WAF Protection Will Be Left Behind In 2020
The big data revolution has changed the way people do business online, but it has also inevitably given rise to…
How to Properly Protect Data on a Crypto Exchange
We live in the age of the cryptocurrency craze, which has brought on a new level of complexity to cybersecurity.…
Potential Hurdles Limiting the Internet of Things
The hype surrounding the Internet of Things (IoT) is immense. The basic premise behind the IoT is to connect everyday…
How Big Data Provides A Pivotal Foundation For VPN Data Security
Americans are overwhelmingly concerned about online privacy. In December, a poll found that only 8% of Americans did not support…
4 Brilliant Ways To Use Big Data To Boost Gmail Security
Google is taking privacy more seriously these days. Last year, the Washington Post reported that they adopted some new big…
4 Ways Big Data Has Made Bluetooth A Terrifying Security Risk
Big data has created both positive and negative impacts on digital technology. On the one hand, big data technology has…
Big Data Heightens The Race Between Proxies And VPNs
Big data is having a profound effect on the privacy debate. The problem is that people only look at it…
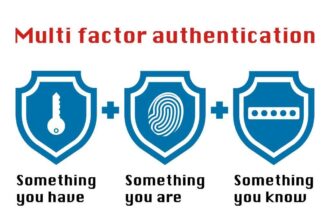
The Relevance of Big Data For Multi-Factor Authentication Solutions
Big data is playing an essential role in authentication. This will become a greater concern than ever, as security risks…
Here’s How VPNs Can Protect Against Big Data Leaks
Virtual private networks (VPNs), can help you unblock content and VPNS can protect you from hackers and shady third-parties. VPNs…
The Impact Of AI On Cybersecurity: Are Humans Still Your Best Asset?
In January, Masergy predicted that 2019 will be ?The Year of Artificial Intelligence.? There?s no question that the term is…